On this post, I’ll try collect some valuable information and put it altogether. I hope it could be useful. All details written are related to vSAN OSA. I’ll try to mention the new vSAN ESA features sometimes, but the intention here is talk about the Original Storage Architecture… so far 😉
vSAN Encryption supports Hybrid and All-Flash vSAN Clusters. This applies for OSA since ESA is only supporting All- flash for the whole Storage Pool. There are vSAN Encryption methods supported, Data-at-Rest Encryption and Data-in-Transit Encryption. Both are configured independent of each other and configured at cluster level. vSAN OSA does a Cluster Wide Encryption. HCI Mesh does not support Data-at-Rest Encryption
Data-In-Transit Encryption:
vSAN can encrypt data in transit, as it moves across hosts in your vSAN cluster. When you enable data-in-transit encryption, vSAN encrypts all data and metadata traffic between hosts. Encrypted vSAN traffic exchanged between vSAN nodes uses a message authentication code to ensure authentication and integrity, then adopts a native proprietary technique to encrypt the vSAN traffic.
Process to encrypt traffic across nodes in the vSAN cluster can be summarized on three main steps:
- A TLS link between vSAN nodes is created to exchange the traffic.
- vSAN nodes create a shared secret and attach it to the current session.
- Uses the shared secret to establish an authenticated encryption session between nodes.
Data-at-Rest Encryption:
vSAN’s Data-at-Rest Encryption securely encrypts vSAN data using AES-256, as it is written to cache and capacity devices. While using this method we get the following:
- Encrypts Data residing on cache and capacity devices
- Supports All-Flash and Hybrid configurations
- Eliminates the need for self encrypting drives
- Validated with FIPS 140-2
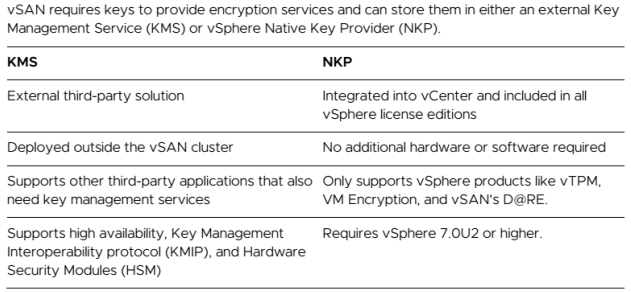
Of course , choosing Data-at-Rest Requires either a Key Manager Service (KMS) or vSphere Native Key Provider (NKP) and it is configured at the cluster level.
vSAN Data-at-Rest Encryption (D@RE) helps protecting against situations of device loss or theft. vSAN D@RE is separate from vSphere VM Encryption (VM Encryption). vSAN D@RE is an inline process which encrypts the data before it lands on a disk. Data is never stored on a disk in an unencrypted state. If an environment is using deduplication and compression or compression-only, encryption occurs after deduplication and compression or compression-only operations, allowing the customer to take advantage of space savings before encrypting. When the data is read, data is decrypted while in transit and returned to the guest OS. The data on the disk remains in an encrypted state.
vSAN encryption is Federal Information Processing Standard (FIPS) 140-2 compliant. FIPS is a joint program between the National Institute of Standards and Technology (NIST) and the Communications Security Establishment (CSE) to set a security standard.
KMS is a solution from an external vendor. The customer needs to decide which product will be using, meaning it needs some research and time to test and maintain it. Nowadays majority of customers finds that encryption does not worth the effort.
As a result, VMware developed vSphere Native Key Provider (NKP). NKP is a solution built into vSphere. NKP requires no additional licenses, external products, or additional clusters. The bar to implementation is very low. NKP goal is to increase adoption of vSAN D@RE.